Blog
Latest news

What is Non-stop Compliance? Models and How to Accomplish It
Continuous compliance refers to the practice of ensuring that an organization consistently adheres to regulatory requirements, industry standards, and internal policies on an ongoing
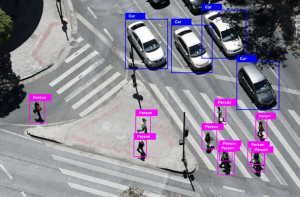
Exploring the Synergy Between Image Annotation and Cybersecurity
Introduction In today’s digital landscape, the importance of cybersecurity cannot be overstated. As technology advances, so do the threats that target our digital assets.

Interoperability and security: why upgraded infrastructure needs both best 3 ways
Interoperability and security: why upgraded infrastructure needs both If you ask 100 people what infrastructure means to them, you’ll get about 99 different answers.

4 Types of best Information Security Services You Need for Your Business
4 Types of Information Security Services You Need for Your Business The threat of Information Security Services -attacks is getting worse every day, and

7 Reasons Why Cybersecurity as a Service is the Best Way to Protect Your Business
7 Reasons Why Cybersecurity as a Service is the Best Way to Protect Your Business You’ve heard the hype surrounding cybersecurity as a service
Information

What is Non-stop Compliance? Models and How to Accomplish It
Continuous compliance refers to the practice of ensuring that an organization consistently adheres to regulatory requirements, industry standards, and internal policies on an ongoing basis.

4 Types of best Information Security Services You Need for Your Business
4 Types of Information Security Services You Need for Your Business The threat of Information Security Services -attacks is getting worse every day, and it’s

Cyber War: Ukraine Proves yes It Needs No Border | 7 different solution hurry!
Cyber War: Ukraine Proves It Needs No Border On July 17, 2015, the personal e-mail accounts of high ranking officers in the Ukrainian military were

3 Ways how to Secure Cyber-Physical Systems Using Threat Modelling
3 Ways how to Secure Cyber-Physical Systems Using Threat Modelling: The market for cyber-physical systems (CPS) is expected to grow by more than 50% in

How Does Cyber Security Work: The Top 8 Ways to Keep Your Data Safe
How Does Cyber Security Work: The Top 8 Ways to Keep Your Data Safe Cybersecurity has become one of the biggest concerns in recent years,

7 Types of Cyber Security Threats
types of cyber security: Everyone’s talking about types of cyber security in the wake of major security breaches at Equifax and other companies, but many

Success with a cyber security apprenticeship system requirements
Success with a cyber security apprenticeship requirements: cyber security apprenticeship: An apprentice, like any other new member of the team who is relatively inexperienced, needs
Technology

What is Non-stop Compliance? Models and How to Accomplish It
Continuous compliance refers to the practice of ensuring that an organization consistently adheres to regulatory requirements, industry standards, and internal policies on an ongoing basis.

When CI ends and CD begins
Continuous Integration and continuous delivery are two inseparable parts of the constant workflow. It enables ongoing automation and monitoring throughout the software development lifecycle. Integrating
EXCLUSIVE Videos

When CI ends and CD begins
Continuous Integration and continuous delivery are two inseparable parts of the constant workflow. It enables ongoing automation and monitoring throughout the software development lifecycle. Integrating
RECOMMENDED FOR YOU

What is Non-stop Compliance? Models and How to Accomplish It
Continuous compliance refers to the practice of ensuring that an organization consistently adheres to regulatory requirements, industry standards, and internal

Exploring the Synergy Between Image Annotation and Cybersecurity
Introduction In today’s digital landscape, the importance of cybersecurity cannot be overstated. As technology advances, so do the threats that

Interoperability and security: why upgraded infrastructure needs both best 3 ways
Interoperability and security: why upgraded infrastructure needs both If you ask 100 people what infrastructure means to them, you’ll get

4 Types of best Information Security Services You Need for Your Business
4 Types of Information Security Services You Need for Your Business The threat of Information Security Services -attacks is getting

7 Reasons Why Cybersecurity as a Service is the Best Way to Protect Your Business
7 Reasons Why Cybersecurity as a Service is the Best Way to Protect Your Business You’ve heard the hype surrounding

The Top 5 Cyber Monitoring Tools to Keep Your Business Safe
The Top 5 Cyber Monitoring Tools to Keep Your Business Safe Cyber attacks are increasing in frequency and severity, and


